
Dynamic Humanized Auxiliary Function Dental Lab CAD Cam 3D Intraoral Scanner - China Intraoral Scanner, Ai Scan | Made-in-China.com
![Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book] Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/15d23931-4396-4e2e-8b6e-6c4a90c7f021.jpg)
Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]

High Precision "cat's Eye" Auxiliary Scanning Light 2d Barcode Scanner Support Hands-free Mode And Handheld Mode - Tool Parts - AliExpress
Total.js Directory Traversal. Metasploit framework is the most… | by Ashish Bhangale | Pentester Academy Blog







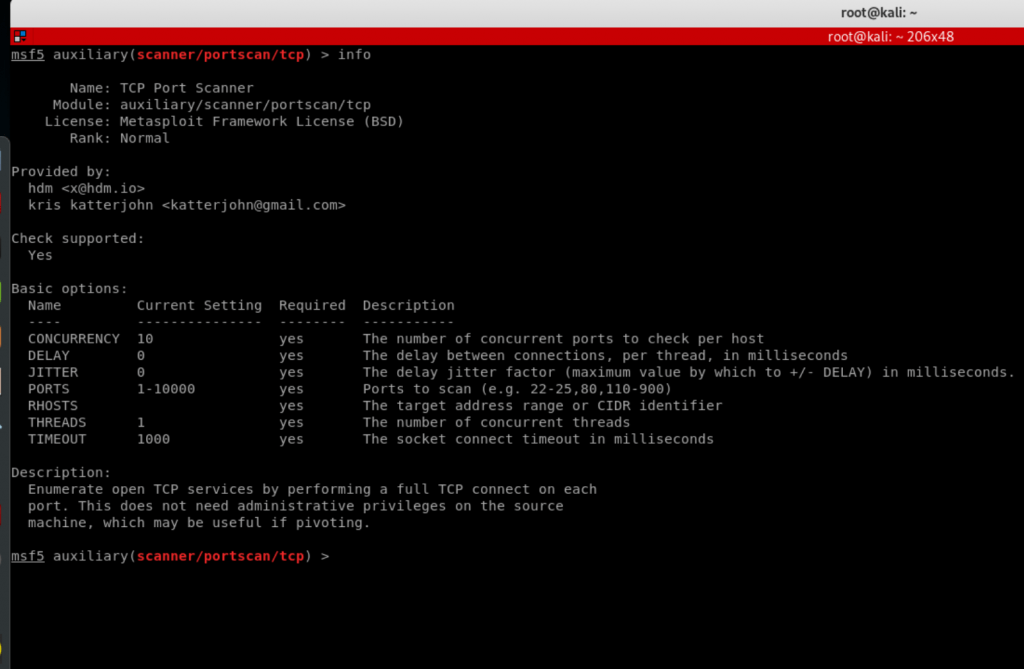
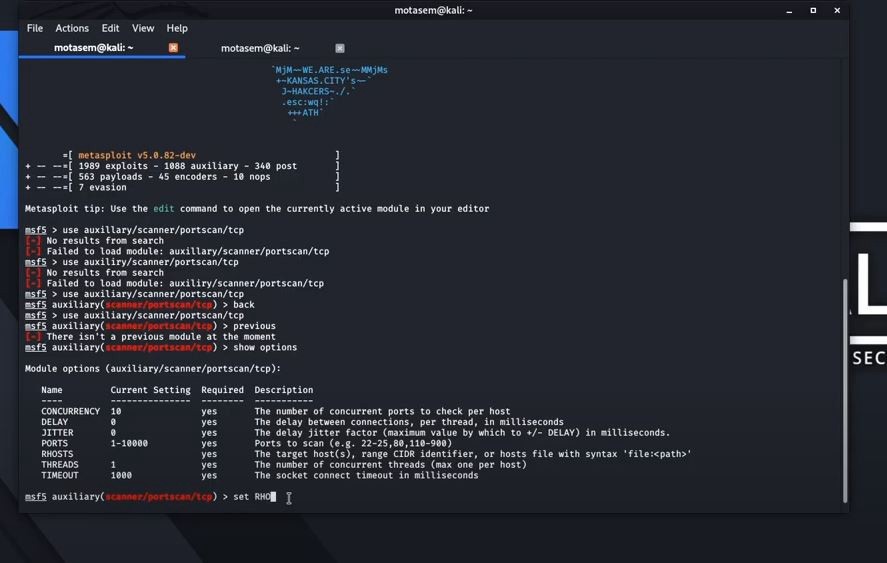

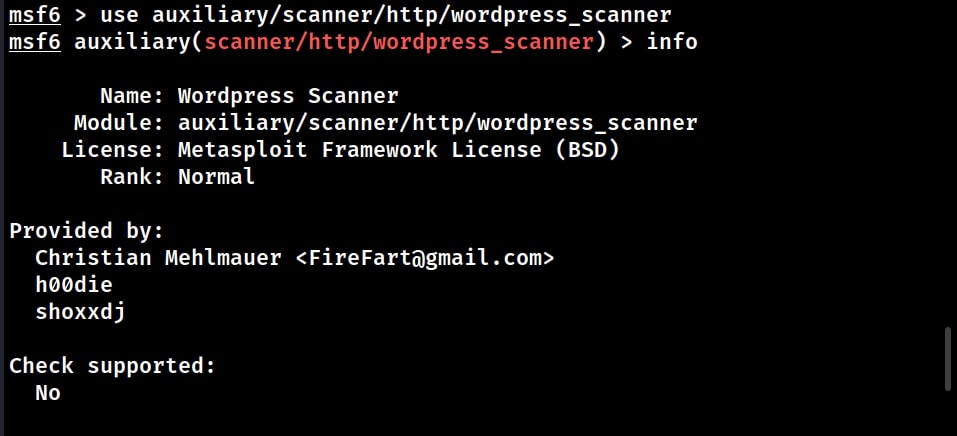





![Vulnerability detection with Metasploit auxiliaries - Metasploit for Beginners [Book] Vulnerability detection with Metasploit auxiliaries - Metasploit for Beginners [Book]](https://www.oreilly.com/api/v2/epubs/9781788295970/files/assets/afb449c4-f990-4f5b-ad6b-a0066c091ae9.jpg)